Author: Wouter
How I am “nicknamed”…
I get that my name is hard to pronounce for non-Dutch speakers. I really do.
I’ve found that it works well if I tell English speakers that my name is “Wow!-ter”, they can remember and pronounce my name near perfectly. “Wow!”, by the way was my nickname in the Authentic World Circling Training T3.

By necessity, I also respond to “Walter”, the common German version of my name (which was amusing when my friend Walter and I went to visit a Japanese customer one time).

However, coffee butchers barristas do manage to misspell my name in some particularly spectacular ways:




And it is not just them. Some graphic designers, who were provided with a spelling out my name and the wish to have a logo for “Wouter.org”, from an account named “Wouter.org” on 99Designs, still manage to translate that an ‘elegant’ “Wolter.org”.

How your body loses heat [spoiler: via arms] (Thunderf00t)
Flip Feng Shui: Perturbation attacks made it to VMs
I’ve been reading up on the Flip Feng Shui: Hammering a Needle in the Software Stack paper, and I’m enjoying that the common smart card attack considerations are coming to more mainstream software considerations.
From the paper:
We describe Flip Feng Shui (FFS), a new exploitation vector that allows an attacker to induce bit flips over arbitrary physical memory in a fully controlled way. FFS relies on two underlying primitives: (i) the ability to induce bit flips in controlled (but not predetermined) physical memory pages; (ii) the ability to control the physical memory layout to reverse-map a target physical page into a virtual memory address un- der attacker control.
This first item we call “perturbation attacks” in smartcard domain. We do those attacks all the time, by giving our poor smartcards power spikes it really shouldn’t be exposed to, prodding it with probing needles too small for the human eye, shooting it with freaking lasers, … you know: standard Monday morning stuff in the office*.
Because we’ve been doing this for ±20 years now in this domain, it takes a while for me to understand a statement like the following is not a joke:
existing cryptographic software is wholly unequipped to counter it, given that “bit flipping is not part of their threat model”.
Because in my world, bit flips are a given, considering that there is an attacker playing with the smartcard. Monday morning remember?
So how does this attack work?
The attack (mis)uses memory de-duplication, i.e. a feature in the host hypervisor that sees that the page of memory of one VM is identical to another one VM’s. When this is enabled, the host hypervisor then maps both these pages to the same page (to reduce actual used physical memory by 40-70%!). If the attacker was the one who created that page originally, he now owns the actual physical page. As long as the host software thinks this page’s content has not changed, the victim VM will read the attacker’s physical page.
So the attacker then does a Rowhammer attack to cause a bit to flip in the part of “his” page. As Rowhammer is a physical side-effect that ‘should not happen’, the host hypervisor does not see the page as changed, even though it is. So now the attacker has just caused a bit flip in his own and, more importantly, this victim’s memory.
Flipping a bit in say a RSA public key allows the attacker to factor that modified key, and generate the appropriate secret key to match. If the attacker does this with the RSA key say used to authenticate root access for SSH, or the signature key for package updates of Linux, he now has full control over that machine.
Neat! (In smartcard world we usually attack the secret key, because of how the protocols are used.)
Theory or practice?
Now, to successfully pull off this attack, several things have to be possible for the attacker:
- predicting the memory content (this excludes attacks on confidential information such as secret keys),
- memory de-duplication must be active (so disabling that, or setting it to “only zero pages”, seems prudent),
- the attacker must be running his VM on the same physical machine as the victim’s VM (I don’t know if this is a realistic scenario. More on it below)
- the memory must be sensitive to something like Rowhammer (so ECC memory is yet again a good idea, it will reduce the chances of this significantly)
Realistic to be the neighbour of your victim VM?
This attack depends on being able to run the attack VM on the same hardware as the victim VM. I have no well-founded grounds to guess if this is a realistic assumption.
I can think of the following situations where that is possible:
- The pool of actual hardware is pretty small compared to the amount of VMs, because the hardware is very beefy or the VMs are small.
- The amount of instances of the victim VMs is pretty big, because it is a standard VM replicated many, many times. I think about situations like massively parallel computing or streaming (Netflix?).
- Or the targeted page is very common, and here I’m thinking of the signature files for updates for example, or company wide backup root accounts.
My conclusion: stay calm and …
Considering all the complexity of this attack, I don’t see it worm all over the Internet soon. It is however a cool warning that attack can and do cross over from these various fields.
I wonder when they’ll realise they can also apply this attack to modify the running code of say the password check routine…
Financial growth to freedom
Lately, I’m getting questions on “how to invest” income beyond direct living costs.
Just like with GTD systems, I find it very important to have a financial system that one can relax into fully. Not having concerns about money frees up a lot of mental and emotional energy, and can shift one from a scarcity to abundance mindset.
My advice and practice is go implement this once the daily living costs have been covered, in the below stated order:
- Put an amount of at least 6 months of living costs + one big unforeseen cost (e.g. suddenly needing a new car due to an accident) aside in a savings account as buffer for hard times.
Taking out a loan is very expensive, both in money (interest) and in energy (loss of abundance mindset). - Invest at least 15% in a financial freedom fund, some form of savings that does not easily lose value but is accessible if you need it within half a year, relative to the way you live.
In my case it is my own house and office, as I don’t likely need to move anytime soon. If you are like a lot of my friends and you want to stay more mobile for a while, consider an investment fund that has the same distribution as the Dow Jones, but mind the costs and risks!! I highly advise reading Tony Robbins’ “Money, master the game” on this topic. Management costs above 0.5% annually of your investment will kill any value accrued. - Invest 10-30% in development of skills and contacts that make you more valuable, more productive and widely skilled, so that you upgrade your market value by at least one order every two years. Examples include workshops that really stretch you beyond what you think you could do or mastermind groups at a level you think is beyond your stature.
After the above, you can put the remainder into further tweaking of your financial growth and stability, with your choice of:
- Extending your safety buffer to 12-24 months (I aim for 18+ months, allowing for a safety margin to abort ventures)
- Reducing any costs you have (e.g. paying off outstanding credit card, loan or mortgage costs)
- Investing in quality products and services that require reduced upkeep costs and make you much more productive
- More investment in financial freedom capital
- More investment in totally different skills and contacts
And whatever you have left and are entirely ok with losing completely, gamble that by:
- Paying it forward to a personally worthwhile social goal. Ideally, this could be bootstrapping someone you personally care about towards their self independence, their growth, while expecting nothing in return (and probably getting a lot from that in feeling good).
- Trying an investment in a start-up you believe in will work financially (with a return of at least 10x) and do your kind of good in the world. Then don’t touch or even look at that investment for at least 5, preferably 10+ years. Don’t expect it to return anything, be positively surprised when it does.
- If you really must learn that lesson yourself: lose it by gambling on the stock market, stepping into or out of the latest crypto coin hype too late, or other such “I can beat the system” delusions.
I hope this view helps you decide wisely where to put your money.
For the growth!
Wouter
Time hack: speeding up podcasts and audiobooks
One of those small hacks that I enjoy a lot, is to set the playback speed of podcasts or audiobooks to 1.5-2x the normal speed. Modern players such as the iOS podcast Overcast app and Audible app will keep the pitch normal.
So the effect is similar to giving the speaker a cup of coffee, not a hit of helium and making him one of the chipmunks. Especially with speakers … who … speak … with … … profound … … silences … like Osho, this speed up saves me a lot of will power to keep listening.
Overcast
The Overcast app has a more granular setting for the speedups. Not only can you select speedups in 0.25 granularity, you can also vary the speedup per podcast (so usually slow speakers can get even higher speedups). In the speedup it also removes the pauses, which gives another 0.25-1.50x speedup without any loss of information.
The Overcast app has a few other features that make life easier: downloading of new episodes is reliable (iOS app is crap at this), skip forward button step is configurable, it automatically plays the next priority episode (iOS app stopped doing this for unknown reasons). And they are very well aware of the impact on our mental well being:
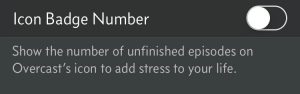
For iOS podcast app
Podcast speed is to the left of the play buttons:
For the Audible app
I like Audible for audiobooks, and quite a few of the speakers have this profound … silence … speaking style that I’m not really interested in anymore, so this works well for me. Tapping on the lower left corner brings up the Narration Speed menu.

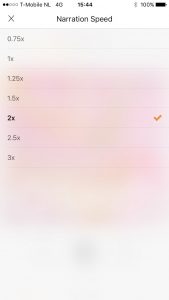

Even more ideal would be removing the silences automatically, similar to how my videos are edited, but I’m not aware of something that does that.
Hoping I saved a few hours of your life with this,
Wouter
NSA Equation Group’s exploits for sale?
There is a persistent and fairly believable rumor going around that a significant amount of the NSA exploits are for sale. To convince potential buyers that they have the goods, the sellers have apparently dumped a ±250MB package of 3-year old exploits and implants for firewalls.
Looking at the descriptions Mustafa Al-Bassam extracted from the dump, it seems plausible that at least these firewall exploits are from a government outfit like the NSA or GCHQ based on the terminology and the typical codenames like “WOBBLYLLAMA”, and the kind of firewalls targeted.
Regardless whether this is the real deal (and whether more than just these firewall exploits are up for grabs), this, in my view highlights the main problems with seeing offensive hacking as as the best defence:
- Backdoors and exploits are often single-use: using them as attacker is risky, as your target may be recording network traffic and recover the attack. This was also explicitly mentioned by Rob Joyce, the head of the NSA’s Tailored Access Operations (TAO) group, i.e. the NSA hackers whose toys are apparently now for sale. Or mishandling a spearfish and lose your nation state quality three 0-days on iOS to Apple, an expensive mistake as a full weaponised remote rooting of iOS is easily $100.000+ value.
As an aside, their 2007 hardware toy catalogue leaked some time ago, a fun read for people like me. - Amusingly, the NSA actually does this eavesdropping to get other organizations’ offensive hacking tools. There are some convincing theories that this ‘leaked exploits sale’ is actually one of the other organisations (China and Russia have been mentioned) getting back at them.
- Somewhere in these offensive organizations there is a weapons cache of these exploits, and it just takes is one disgruntled employee with access to it and the desire to leak it. After all, it is these hackers’ full-time job and passion to break in and out of highly secure environments, and they have all the tools for this. (This is the most likely explanation).
- Once the attacks are out, others can also use it against you! The NSA has the story that “NObody But US” (NOBUS) can exploit these things, and use that as an argument not to inform the American companies whose products are at risk in this way. So now, Cisco (and other) firewall vendors are scrambling to make a bug fix (which takes a few days to weeks), and actually may impact other products too.
Then the users of these firewalls have to actually deploy the bug fix (which they’ll be reluctant to do for reliability reasons, if the users even know that the bug fix exists, taking another few days to many months), and all the while savvy and assertive attackers can hack these firewalls at their leisure.
I still have this naive hope that these blowups will change policy for these organizations to lean to the defensive more. Realistically though, they’ll double down: both hide their exploit development better and come down even harder on leakers and whistleblowers.
And of course thus continues the arms race, making us all less secure in the long term for a short term gain. Sigh.
Your friendly professionally paranoid,
Wouter
P.S. this may of course just be a disinformation campaign or a fundraiser. One never knows… (until ±30-50 years later when the documents get declassified)
Voynich manuscript reproduction coming
Oh, in the world of infinite resources, I definitely lust for this, for the sheer having as a token of cryptography run rampant: The Voynich manuscript is going to be reproduced at a staggering $10,000 price tag.
Much more reasonably priced reprints are available via Yale books or Amazon, and the scans are available for free.
The Voynich manuscript has been intriguing cryptoanalysists for ages, with its cryptic almost-sensible texts, pictures of not-quite-real plants and animals. There are interesting attempts claiming to have partially decoded it here and here.
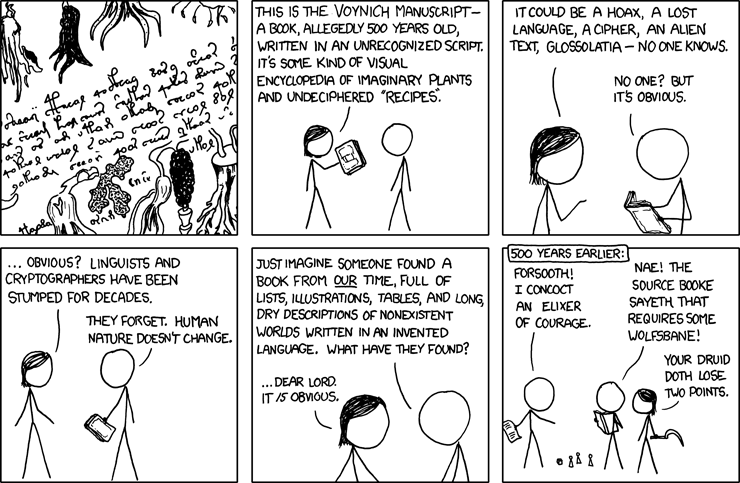
I, for one, think XKCD still has the best explanation of the origins of this intriguing manuscript:
Random encounter: Conservative Republican meets a Dutch socialist on the plane
I love random encounters.
I had a delightful and insightful conversation with a honest-to-God bible-thumping conservative Republican, my neighbor on one of my flights within the US.
Yes, he believed LBGTQ folks are devilish and all, but I understood where he was coming from. And he asked and tried to understand where I was coming from also. I think we both left with a better insight of the culture we each live in.
Typical moment:
Him: So do those gays also rub your face into it so much over there in Europe?
Me: Hmmm, well, we’ve had gay rights movement since the late ’70s early ’80s and gay marriage for over 15 years, so there isn’t that much to rub our face into. LBGTQ folks are pretty mainstream.
Him: Huh, I guess that works too…
This random encounter left me with a better understanding of this person I would have judged not worth talking to if I had followed my prejudices. He had a company in company catering and clearly cared deeply for his ±100 employees: paying them well above industry norms, arranging lots of support for them. He selected his clients on how well they would treat his employees, whether they saw his employees as a cost to the company or a benefit to their employees.
And yes he as doing lots for charity. He just wanted to be able to decide himself where to put his money towards.
In short, I met the conservative philanthrope of Ayn Rand in person.
He I hope got a bit of relaxed “we can all get along” from this lefty, and got that over in Europe we’re not taxed to death as much as Fox news makes it look.
It was a good meeting in the air,
Wouter
How long to try a venture?
I’m getting quite a few questions recently about being an entrepreneur, and a specific recurring question is: so I have put my hopes on this venture, it might not take off soon, should I go for it?
To which my answer is a version of: check if you can afford to give the venture your all for 0.5-1.5 years, and that you have enough money available to last 0.5 years after that. If yes on both of these, go for it. If you’re unsure on any of these, reconsider. Read further for more detail…
Background
This is coming from theory and quite a bit of practice: I’ve had my own company for more than 20 years (since 1995-08-08), and during that time, I have at times been employed with other companies also (see my resume for the details).
I’ve had “Really well thought out!” and “What was I thinking?” ventures over the years, and a significant amount of them did become successful within the specified trial time frame I set for it (this blog and Authentic Europe for example). I’ve also, often with pain in my heart, decided I should and would not go fully with other projects, because I did not have the finances for it.
And at the same time I’ve seen quite some people try things half-baked and fail, I’ve seen too many people run themselves into trouble by not considering beforehand how to stop, and none of them ended well.
All of this to say, that I’ve both thought a lot about this topic, and seen it play out real time.
So this post is about how to determine how long to try to make a venture work, and when to stop, in service of both you and your venture getting a fair chance.
Try the venture at least 0.5-1.5 years…
A venture needs time to be developed, deployed and especially to be marketed and sold. This time frame is best counted in months as there is often a lag time of 3-6 months between a customer becoming convinced he needs the offering, and actually receiving the money in the bank account, particularly for service offerings.
For example, a typical and fairly optimal time frame for a customer wanting a training workshop from me looks like this:
- Week 00: First contact, customer sends request for training workshop, I send clarification questions.
- Week 01: Their partial answer comes in. I make an estimate on what workshop would fit best and send it for discussion/agreement.
- Week 04: My response and some negotiation on terms.
- Week 05: My offer is sent to the client.
- … silence (The contact person is gathering the signatures and budget from within the bureaucracy of the organization.)
- Week 07: Signed contract. (If the legal or financial departments are involved, add 2-3 weeks at least, in mutual negotiation of the planning of the workshop.)
- Week 11: Workshop takes place, at least one month out, as it needs to be customized. (In practice my agenda is nowadays usually full for the first ±2-3 months, but that is another discussion.)
- Week 15-23: Payment received. (Most big organizations have 30-90 days after delivery payment terms.)
The above timeline does not include the time gap between promoting myself and the customer actually coming to me, which is at least a few months, if not a few quarters. At least 30% of my CC training customers decided that they wanted a training from me 1-2 years ago.
Thus, seeing the above timeline, means that you have to give any venture at least 0.5-1.5 years to see if it is going to work out. You should be a “hell YES!” to this.
Anything less than a resounding “YES!”:
- Put the venture idea in your “sometime maybe” GTD file and save up, or
- Consider re-engineering the venture to either feel like a “YES!” or consider running it as a low-intensity experiment alongside an existing job, or
- Hand it over to someone else.
… But make sure your money stretches that long!
So you determined you can give the venture the time it needs to succeed? Now you have to check that you have the money to make it to that end, or safely land if you can’t make the venture work.
“The venture works” when it is sustaining you financially for a good hourly rate. You should decide now to stop the venture if that deadline is reached, and go seek other sources of income such as a job.
You’ll want to have enough finances available now to last you until at least 3, preferably 6, months of living costs after the deadline for the venture. At least 3, because even when you are in extremely high demand on the workforce, it will take a month for you to be hired, and a month for you to be paid at the very least. Realistically you should have more like 6 months of safety margin.
Conclusion: Fail fast or at its due time
So my advice is to look hard at venture ideas and ask yourself if you believe enough in it to commit 0.5-1.5 years to it.
Then set a limit on how long you are going to try the venture, by making sure you’ll have enough finances presently available, to allow at least 3 months of living costs after the deadline for the venture.
Good luck with your venture, and well done if you reconsidered!
Wouter